How to Use Campaign Monitoring Tools for Better Results is essential for anyone looking to enhance their marketing efforts. In today’s fast-paced digital landscape, effective monitoring tools play a crucial role in measuring the success and impact of your campaigns. From tracking key performance indicators (KPIs) to analyzing audience engagement, these tools offer invaluable insights that can steer your strategies in the right direction.
Understanding how to leverage these tools can lead to more informed decisions and ultimately drive better results. Whether you’re managing a small business or a large corporation, utilizing campaign monitoring tools can elevate your marketing game and help you connect with your audience more effectively.
In the ever-evolving landscape of technology, the importance of cybersecurity has surged to the forefront of both personal and professional realms. As we navigate through an age characterized by digital transformation, the potential threats posed by cybercriminals have become increasingly sophisticated. This article aims to shed light on various aspects of cybersecurity, including its significance, common threats, and best practices to protect both individuals and organizations.### The Significance of CybersecurityCybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks.
These attacks are primarily aimed at accessing, altering, or destroying sensitive information; extorting money from users; or interrupting normal business processes. With the growing reliance on technology, the importance of cybersecurity cannot be overstated. In today’s interconnected world, individuals and organizations store sensitive data online, which can include personal information, financial records, and proprietary business information. A data breach can lead to severe consequences, including financial loss, reputational damage, and legal repercussions.
Therefore, implementing robust cybersecurity measures is not just a luxury but a necessity.### Common Cybersecurity Threats
1. Malware
Short for malicious software, malware is designed to disrupt, damage, or gain unauthorized access to computer systems. This includes viruses, worms, and ransomware. Ransomware, for example, encrypts files on a victim’s device, demanding a ransom for their release.
2. Phishing
Phishing is a social engineering attack where attackers impersonate legitimate organizations to trick individuals into providing sensitive information. This can occur through deceptive emails, messages, or websites that appear trustworthy.
3. Denial of Service Attacks (DoS)
In a DoS attack, the perpetrator aims to make a machine or network resource unavailable by overwhelming it with traffic. This can disrupt services and lead to significant downtime.
4. Man-in-the-Middle Attacks
In this type of attack, an attacker secretly intercepts and relays messages between two parties who believe they are directly communicating with each other. This can happen through unsecured Wi-Fi networks, where attackers can easily eavesdrop.
5. Insider Threats
Sometimes, the threat comes from within an organization. Employees or contractors may intentionally or unintentionally compromise security, often due to negligence or lack of awareness.### Best Practices for CybersecurityTo defend against these threats effectively, individuals and organizations can adopt several best practices:
1. Educate and Train Employees
Regular training sessions on cybersecurity awareness can empower employees to recognize and respond to potential threats. This should include guidance on identifying phishing attempts and the importance of strong passwords.
2. Implement Strong Password Policies
Strong, unique passwords should be enforced for all accounts, and two-factor authentication (2FA) should be enabled wherever possible. This adds an extra layer of security by requiring a second form of verification in addition to the password.
3. Regular Software Updates
Keeping software and systems up to date is crucial to closing security vulnerabilities that attackers may exploit. This includes updating operating systems, applications, and antivirus programs.
4. Use Firewalls and Antivirus Software
Firewalls act as a barrier between trusted internal networks and untrusted external networks, helping to prevent unauthorized access. Antivirus software can detect and eliminate malware before it causes harm.
5. Backup Data Regularly
Regularly backing up important data ensures that, in the event of a cyberattack, critical information can be restored with minimal disruption. It’s advisable to keep backups in a secure, off-site location.
6. Monitor Network Traffic
Utilizing tools to monitor and analyze network traffic can help identify unusual patterns or unauthorized access attempts, allowing for swift action to be taken.
7. Develop an Incident Response Plan
Having a well-defined incident response plan in place can significantly reduce the impact of a cyberattack. This plan should Artikel the steps to take when a security breach occurs, including communication strategies and recovery processes.### The Role of Government and RegulationsGovernments around the world are increasingly recognizing the need for stringent cybersecurity regulations to protect citizens and businesses alike.
Laws such as the General Data Protection Regulation (GDPR) in Europe, the Health Insurance Portability and Accountability Act (HIPAA) in the United States, and various other national and industry-specific regulations impose requirements on organizations to protect sensitive data.These regulations not only mandate organizations to implement specific security measures but also enforce penalties for non-compliance. This creates a framework that encourages businesses to prioritize cybersecurity as a key component of their operations.### The Future of CybersecurityAs technology continues to advance, the cybersecurity landscape will likely become more complex.
The rise of artificial intelligence (AI) and machine learning (ML) brings both opportunities and challenges. While these technologies can enhance security measures by analyzing vast amounts of data to detect threats, they can also be leveraged by cybercriminals to launch more sophisticated attacks.Additionally, the growing trend of remote work and the Internet of Things (IoT) further complicates the cybersecurity landscape.
With more devices connected to the internet and employees working from various locations, the potential attack surface has expanded dramatically.### ConclusionIn conclusion, cybersecurity is an essential aspect of modern life that must be prioritized by individuals and organizations alike. The threats are real and constantly evolving, making it imperative to stay informed and proactive in implementing security measures. By understanding the significance of cybersecurity, recognizing common threats, and adhering to best practices, we can all contribute to a safer digital environment.As we look to the future, continued investment in cybersecurity education, technology, and regulatory frameworks will be crucial in safeguarding our digital assets.
The responsibility lies with each of us to foster a culture of awareness and vigilance, ensuring that we are well-equipped to face the challenges that lie ahead in the cybersecurity arena.
Common Queries: How To Use Campaign Monitoring Tools For Better Results
What are campaign monitoring tools?
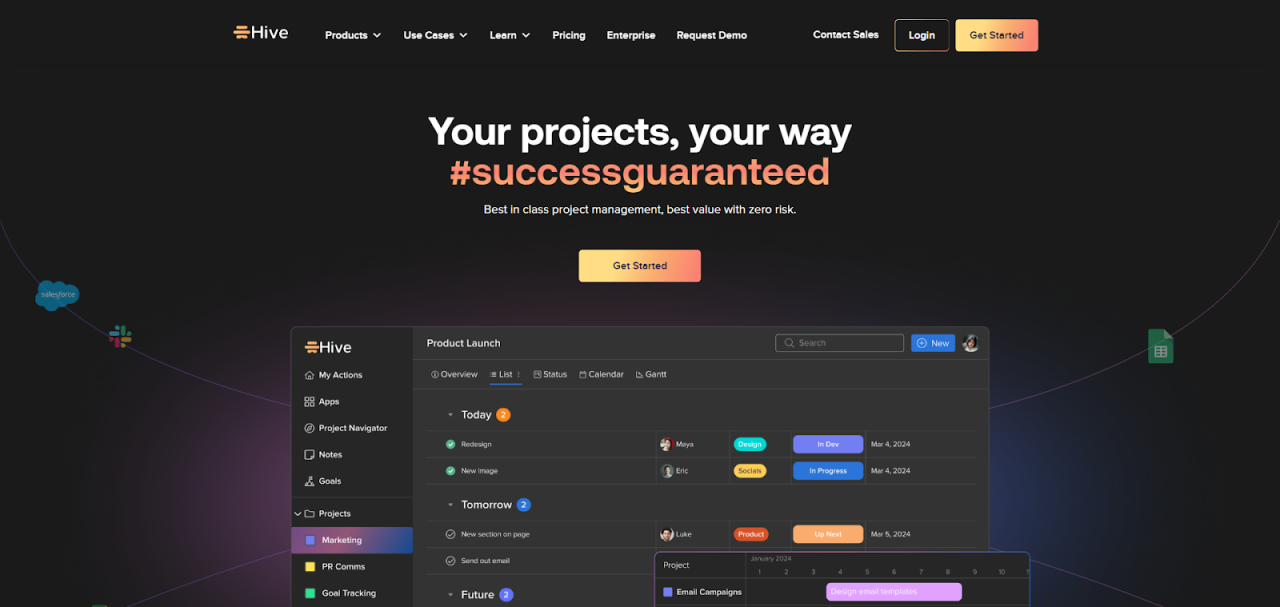
Campaign monitoring tools are software applications that help marketers track and analyze the performance of their marketing campaigns.
How can I choose the right monitoring tool for my needs?
Consider your specific goals, budget, and the features offered by different tools to find one that aligns with your needs.
Can campaign monitoring tools integrate with other software?
Many campaign monitoring tools offer integration with CRM and other marketing software to streamline your processes.
How often should I check my campaign metrics?
Regularly checking your metrics, ideally in real-time or weekly, allows you to make timely adjustments to your campaigns.
Are there free campaign monitoring tools available?
Yes, there are several free options available that offer basic features for monitoring campaign performance.






